Authentication
The BOSS API uses a combination of the Azure AD B2C and a subscription key to authenticate requests. BOSS consumers will use Azure B2C to retrieve an JWT bearer token. The client credentials (to retrieve the bearer token) and the subscription key will be provided during the onboarding process.
The following diagram shows how the authentication works:
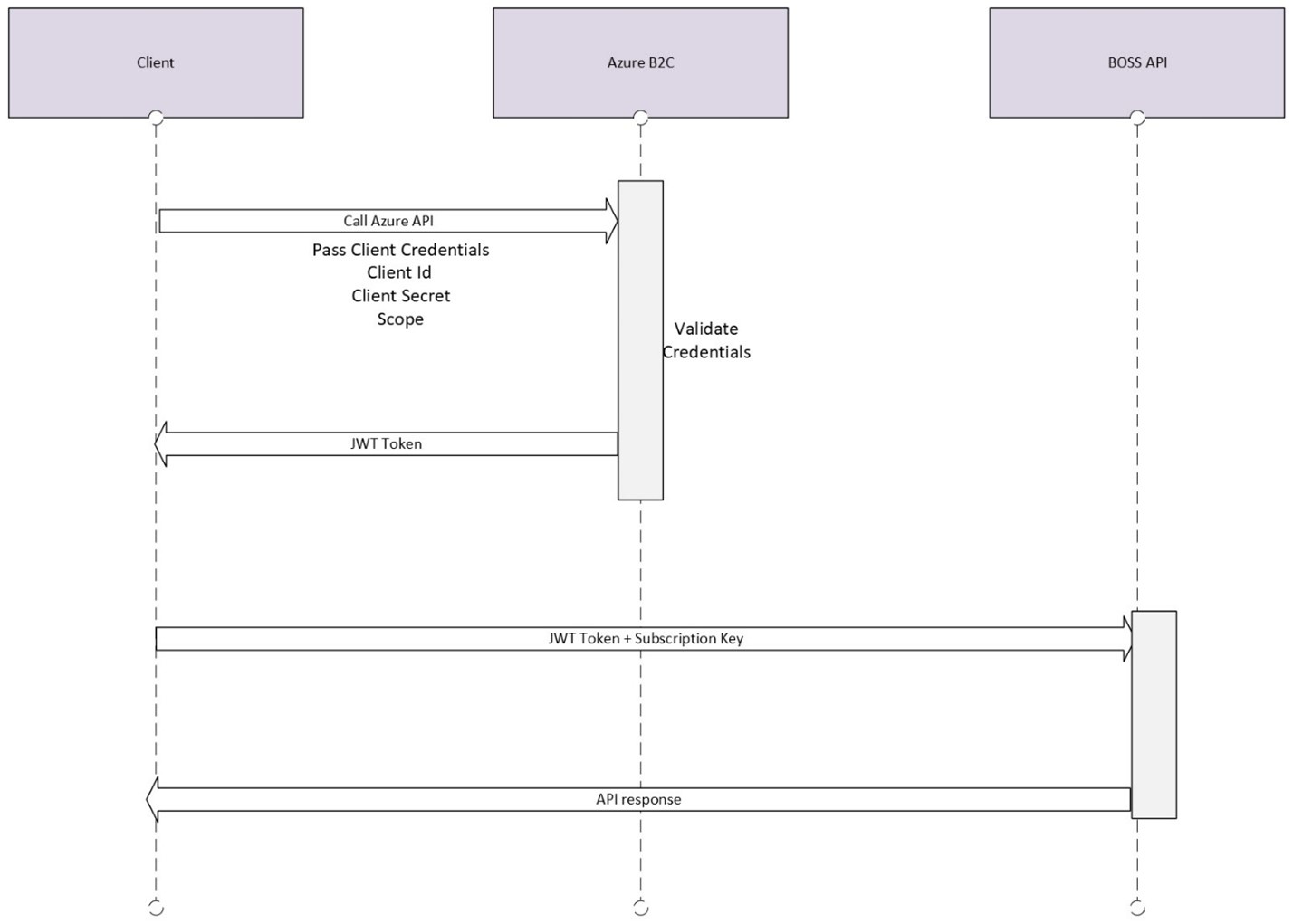
1. The application requests an JWT token from the Azure B2C URL by sending a request with its client_id, client_secret, scope and the grant_type (client_credentials).
2. The identity server authenticates the client and verifies that it has the necessary permissions to access the requested resources.
3. If the client is successfully authenticated, the authorization server issues an JWT token, which the application can use to access the protected resources on the service.
4. The application sends the subscription key and the JWT Token in the Authorization header of subsequent requests to the service's resource server and the server grants access if the token is valid.
Access Token Request Details
Environment URLs
NonProd
Prod
https://login.orders.com/e940936e-3b4d-4248-9fb6-1ba0ad45fef6/b2c_1_taylor_integrations/oauth2/v2.0/token
The service endpoints will by default support 120 requests per minute per client. Any request beyond that will return a 429 HTTP error.
Access Token Request Example
The examples below show how to request the JWT token. The property ‘access_token’ is what needs to be extracted from the JSON response. This value will be used in the Authorization header when calling the API endpoints.
The expiration of the tokens is defined in the field ‘expires_in’ (3600 = 1 hour). You will want to persist the token for its lifetime to make your application more performant.
{
"access_token": "eyJhbGciOiJSUzI1NiIsImtpZCI6Ilg1ZVhrNHh5b2pORnVtMWtsMll0djhkbE5QNC1jNTdkTzZRR1RWQndhTmsiLCJ0eXAiOiJKV1QifQ.eyJhdWQiOiJodHRwczovL2VudGFwcHNsb2dpbnNhbmRib3gub25taWNyb3NvZnQuY29tL0JPU1NDdXN0b21lckFwaSIsImlzcyI6Imh0dHBzOi8vZW50YXBwc2xvZ2luc2FuZGJveC5iMmNsb2dpbi5jb20vY2FlMDhkODEtNTQ5MC00MzJkLTg4YTYtYjY4ZTI3NWEzYjI5L3YyLjAvIiwiZXhwIjoxNzI5MTE3MjQ5LCJuYmYiOjE3MjkxMTM2NDksInRmcCI6IkIyQ18xX1RheWxvcl9JbnRlZ3JhdGlvbnMiLCJzY3AiOiJzY29wZS50Y19ib3NhcGlfYXV0aF9za3VfY3JlYXRlIHNjb3BlLnRjX2Jvc2FwaV9hdXRoX29yZGVyX3JlYWQgc2NvcGUudGNfYm9zYXBpX2F1dGhfc2t1X3VwZGF0ZSBzY29wZS50Y19ib3NhcGlfYXV0aF9vcmRlcl91cGRhdGUgc2NvcGUudGNfYm9zYXBpX2F1dGhfYWxsX29yZ2FuaXphdGlvbl9yZWFkIHNjb3BlLnRjX2Jvc2FwaV9hdXRoX3NrdV9yZWFkIFRDX09yZGVyQWdlbmN5LnRlc3Qgc2NvcGUudGNfYm9zYXBpX3BvX3ZhbGlkYXRpb24gc2NvcGUudGNfYm9zYXBpX2F1dGhfY2FjaGVfdXBkYXRlIHNjb3BlLnRjX2Jvc2FwaV9hdXRoX29yZGVyX2NhbmNlbCBzY29wZS50Y19ib3NhcGlfYXV0aF92ZW5kb3Jfb3JkZXJfcmVhZCBzY29wZS50Y19ib3NhcGlfYXV0aF9vcmdhbml6YXRpb25fcmVhZCBzY29wZS50Y19ib3NhcGlfYXV0aF9vcmRlcl9jcmVhdGUgc2NvcGUudGNfYm9zYXBpX2F1dGhfc2t1X2RlbGV0ZSBzY29wZS50Y19ib3NhcGlfYXV0aF92ZW5kb3JfcmVhZCIsInN1YiI6Ijg3Y2ViYmQ4LTc2YTEtNDc1MC04YTRlLTRmM2I5NTk4YmZmMiIsIm9pZCI6Ijg3Y2ViYmQ4LTc2YTEtNDc1MC04YTRlLTRmM2I5NTk4YmZmMiIsInRpZCI6ImNhZTA4ZDgxLTU0OTAtNDMyZC04OGE2LWI2OGUyNzVhM2IyOSIsInZlciI6IjEuMCIsImF6cCI6ImFlMWJjYmJhLTYxMmMtNGIyMC04OTNkLTE1ZDQ1OTk4MDVmNiIsImlhdCI6MTcyOTExMzY0OX0.LE_5RIjSdzWbsqZil-JFX_IsfAkYe9xHHobBZyUe64n2sq4C7B_N27h6jkLugquVql0dxtFxmVOWILiN_q1DZ1NbNkJWNqQpvKQYjTZBCDcFJnmxxbBdBuOWfhhSBPQ-R79KVAZvnERq1GYrQcr-o7GMmMFtbUWcCXI6uWofjyGmi-jqtwcWd57yP98BYB5YdKoO6y1iEY384nwdXV7AjvMhMkMBZIdGCJgBzal9pRRW5_B6jdpfseqsIrcU_Wg2T1iKFDYOm3VKmMBvxPICJLs5k77MvXJlQTQCEC9UCtx35z34qRMGtgpwV4l4DIsHAEx87cy8drcQotGBR6Khsg",
"token_type": "Bearer",
"not_before": 1729113649,
"expires_in": 3600,
"expires_on": 1729117249,
"resource": "https://entappsloginsandbox.onmicrosoft.com/BOSSCustomerApi"
}
Curl Example
Subscription Key
The subscription key is provided during the onboarding process and is used in combination with the access_token when making a call against the BOSS API the curl
The curl example below shows the use of the subscription key (Ocp-Apim-Subscription-Key) when performing a call against the API.
Scopes
BOSS API scopes are used to define the level of access for specific resources. They server as a security mechanism to restrict access to certain parts of the API. Scopes are defined in the Identity Service Provider and can be requested by the client during the authentication process. The table below describes the different scopes for the BOSS API.
POST Order: API call used to submit an order for an item with variable details (e.g.: Personalized business cards or gift card holders not ordered through a navINK configurator).
Operation: POST (Submit Order)
Azure SCOPE: tc_darkseid_auth_order_create and tc_bosapi_auth_order_create
